Definition
A security incident is any action that threatens one or more of the classic security services of confidentiality, integrity, availability, accountability, authenticity, and reliability in a system.
The term used to describe the development of procedures for handling and responding to computer incidents is incident response. These procedures should take into account the potential consequences of an incident on the organization and provide an appropriate response. Incident response offers several benefits, including:
- Ensuring a systematic response to incidents, ensuring that the necessary steps are taken.
- Facilitating quick and efficient recovery for personnel, minimizing the loss or theft of information and the disruption of services.
- Properly addressing legal issues that may arise.
- Utilizing the information gathered during incident handling to improve preparedness for future incidents and enhance the protection of systems and data.
Mass email worm infections
A mass email worm infection may work as follows:
- exploit unpatched vulnerabilities in desktop applications and then spread via email;
- the volume of traffic these can generate could be high enough to cripple both intranet and internet connections.
The obvious response is to disconnect the organization from the internet and shut down the internal email system. However, this would have a serious impact on the organization’s processes. Therefore, a trade-off between major loss of functionality and further significant systems compromise is needed.
A good incident response policy should indicate the action to take for an incident of this severity, specify the personnel who have the responsibility to make decisions, and detail how they can be quickly contacted.
Managing security incidents involves procedures and controls that address detecting potential security incidents, sorting, categorizing, and prioritizing incoming incident reports, identifying and responding to breaches in security, and documenting breaches in security for future reference. The goal is to minimize the impact of security incidents on the organization and to prevent future incidents.
Definitions
- Artifact: any file or object found on a system that might be involved in probing or attacking systems and networks or that is being used to defeat security measures.
- Computer Security Incident Response Team (CSIRT): a capability set up for the purpose of assisting in responding to computer security-related incidents that involve sites within a defined constituency, also called CERT, or with other acronyms. The CSIRT is responsible for:
- rapidly detecting incidents;
- minimizing loss and destruction;
- mitigating the weaknesses that were exploited;
- restoring computing services.
We define the following terms:
- Constituency: the group of users, sites, networks, or organizations served by the CSIRT.
- Incident: a violation or imminent threat of violation of computer security policies.
- Triage: the process of receiving, sorting, and prioritizing information to facilitate its appropriate handling.
- Vulnerability: a weakness in the system that can be exploited to violate the CIA constraints.
Detecting incidents
Security incidents can be identified through various means, including:
- User reports: Users who notice system malfunctions, anomalous behavior, or weaknesses should be encouraged to report them. Proper training can help raise awareness among staff members.
- Automated tools: Analyzing information collected from systems and connected networks using automated tools can also help detect security incidents. Automated tools for incident detection can be categorized as:
- system integrity verification tools: scan critical system files, directories, and services to ensure they have not been changed without proper authorization;
- log analysis tools: analyze the information collected in audit logs using a form of pattern recognition to identify potential security incidents;
- network and host intrusion detection systems (IDS): monitor and analyze network and host activity and usually compare this information with a collection of attack signatures to identify potential security incidents;
- intrusion prevention systems (IPS): augment an intrusion detection system with the ability to automatically block detected attacks.
Automated tools play a crucial role in incident detection, but they require regular updates and accurate configuration to effectively differentiate between normal behavior and potential attacks. However, their deployment should be approached with caution due to the significant resources, both financial and personnel, involved. The effectiveness of these tools relies on the correctness of patterns and signatures used, and they should be regularly updated to keep up with evolving security risks.
Security administrators often struggle to keep up with the rapidly changing security landscape and respond promptly. Automated tools can help mitigate risks by tracking changes in known attacks and enabling timely responses.
The decision to implement automated tools should be based on the organization’s security goals, objectives, and the specific needs identified during the risk assessment process.
Triage function
The triage function is responsible for receiving, sorting, and prioritizing information to facilitate its appropriate handling.
Goal
Ensure that all information destined for the incident handling service is channeled through a single focal point regardless of the method by which it arrives for appropriate redistribution and handling within the service.
The triage function responds to incoming information by:
- requesting additional information to categorize the incident and determine its priority;
- notifying the enterprise about known vulnerabilities and sharing information about how to fix or mitigate them to prevent future incidents;
- identifying the incident as either new or part of an ongoing incident and passing this information on to the incident handling response function in priority order.
Responding to incidents
Upon the detection of a potential incident, it is essential to have established, documented procedures for an effective response. This response may involve several key actions, including initiating prompt measures to secure affected systems and networks from unauthorized access, deploying appropriate alerts and mitigation strategies to address the issue, and conducting comprehensive investigations to uncover any intruder activity across other areas of the network. Additionally, it may involve filtering network traffic to prevent further compromise, reconstructing systems or applying necessary patches and repairs, and formulating alternative response strategies or workarounds.
The response procedures should:
- Clearly identify the cause of the security incident (whether accidental or deliberate), categorize the incidents, outline the approach to respond to them, specify the responsible management personnel for critical decision-making, provide contact information for them, and define the circumstances under which security breaches should be reported to third parties.
- Describe the actions taken to recover from the incident, with the goal of minimizing the impact or harm to the organization.
- Collect evidence of the incident, which can aid in the recovery process and potentially be used in legal proceedings if the incident is reported to the police.
When addressing incidents, it is crucial to consider a range of factors that can significantly influence the outcome. These factors include the critical role that the affected system plays in the organization’s operations, alongside both the immediate and potential technical consequences of the incident, with particular attention to the extent of system compromise. Understanding these elements allows for a more precise assessment of the situation. Consequently, the response strategy should be carefully tailored to the specific circumstances of the incident and aligned with the organization’s unique needs and operational priorities.
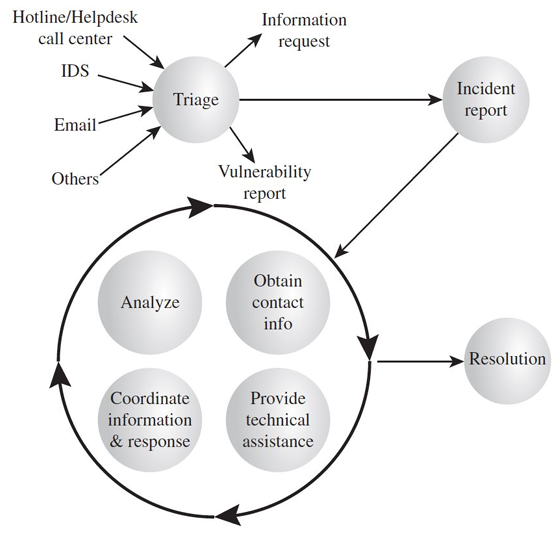
The incident handling life cycle is a recurring process in IT security management. It entails identifying the vulnerability that caused the incident, finding ways to address it to prevent future incidents, documenting the incident and the response for future reference, and reassessing the impact on the organization’s systems and their risk profile as a result of the incident.
| Service Name | Information flow to incident handling | Information flow from incident handling |
|---|---|---|
| Announcements | Warning of current attack scenario | - Statistics or status report - new attack profiles to consider or research |
| Vulnerability Handling | How to protect against exploitation of specific vulnerabilities, possible existence of new vulnerabilities | Possible existence of new vulnerabilities |
| Malware Handling | - Information on how to recognize use of specific malware - information on malware impact/threat | - Statistics on identification of malware in incidents - new malware sample |
| Education/Training | Practical examples and motivation knowledge | |
| Intrusion Detection Services | New incident report | New attack profile to check for |
| Security Audit or Assessments | Notification of penetration test start and finish schedules, common attack scenarios | Common attack scenarios |
| Security Consulting | Information about common pitfalls and the magnitude of the threats | Practical examples/experiences |
| Risk Analysis | Information about common pitfalls and the magnitude of the threats | Statistics or scenarios of loss |
| Technology Watch | Warn of possible future attack scenarios, alert to new tool distribution | Statistics or status report, new attack profiles to consider or research |
| Development of Security Tools | Availability of new tools for constituency use, need for products | Provide view of current practices |