Bitcoin
Definition
Bitcoin is an information technology breakthrough that define and implement a secure, decentralized payment system and a tool for the storage, verification and auditing of information, including digital representations of values. Its protocol defines an overlay network over Internet that mine bitcoins, each node manage a group of addresses that holds coins, each address is a hashed image of an underlying private-public pair of cryptographic keys and act as a pseudonym of the coin’s holder.
The nodes view of this common state is formed by a Blockchain, a shared, append-only, trustable, ledger of all coins transactions. The limits of distributed consensus defined in the Byzantine Problem and CAP Theorem are solved using the technique of proof-of-work.
Definition
Bitcoin wallet is a software that allows to manage and store the public and private key for each of your bitcoin addresses, create and sign transactions (receive or spend BTC), and track the balance (log of all of your incoming and outgoing transactions).
Each user has a public BTC address assigned to them. The BTC public address is an alphanumeric string from 26 to 35 characters used to receive payments (unique identifier that links transactions with sender and receiver). An example of a BTC address is:3D2oetdNuZUqQHPJmcMDDHYoqkyNVsFk9r.
The BTC private key is a 256-bit number that allows to spend the BTC associated with the public address. The private key is used to sign the transaction and is never shared with anyone. The private key is used to generate the public key, which is used to generate the public address. The public key is used to verify the signature of the transaction, while the public address is used to receive the BTC.
A particular characteristic of the Bitcoin protocol is that there is no amount of BTC stored in the wallet, instead there is a list of transactions that are linked to the public address. The amount of BTC that a user has is the sum of all the transactions that are linked to the public address.
Bitcoin transaction lifecycle
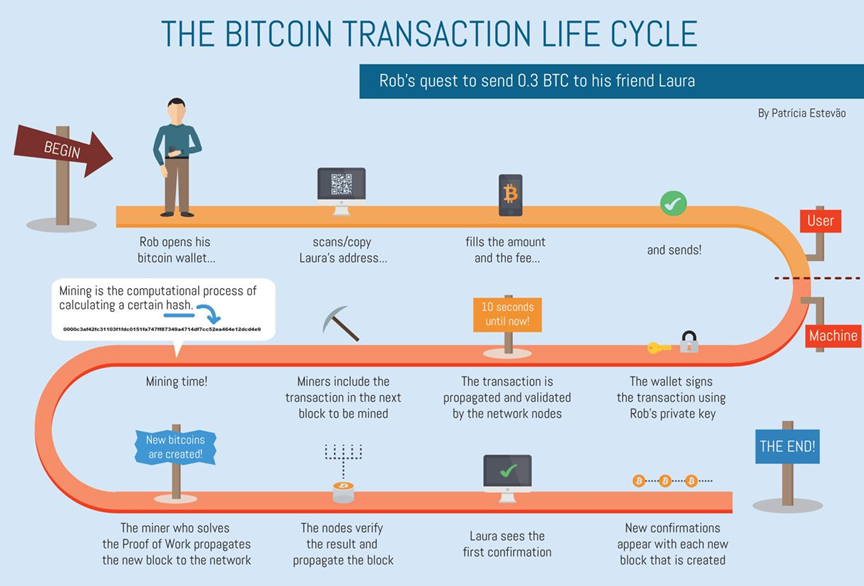
- User opens his wallet in, if he has no address, he generates one.
- User scans the QR code of the seller’s address.
- User fills the amount and the fee associated with the transaction, and sends it to the seller.
- On the machine side, the wallet signs the transaction with the private key and sends it to the network.
- The transaction is propagated to the blockchain and validated by the netwrok nodes
- The transaction is included in a block by a miner and the block is added to the blockchain.
- The mining process require to solve a complex mathematical problem in order to produce a new block (Proof-of-Work).
- The nodes verify the result of the miner and propagate the new block to the network.
- The transaction is confirmed and the seller can see the transaction in his wallet.
- New confirmations appear with each new block that is added to the blockchain.
Transaction workflow
In the Bitcoin ecosystem, each transaction consists of four essential elements:
- The previous transaction hash (txid): This is a unique identifier that references the previous transaction from which the sender received the bitcoins.
- The receiver’s public key: This is the public key associated with the recipient’s Bitcoin address. It is used to verify the authenticity of the transaction.
- A hash function: This function links the previous transaction hash with the receiver’s public key, ensuring the integrity of the transaction history.
- The previous owner’s signature: This is generated using the sender’s private key and serves as proof of ownership and authorization for the transaction.
flowchart LR subgraph Z[Transaction to Joe] A[Joe's<br>public key] --> B[Hash] --> C[Previous owner's sign] end subgraph X[Transaction Joe -> Alice] E[Alice's<br>public key] --> F[Hash] --> G[Joe's sign] end subgraph Y[Transaction Alice -> Bob] I[Bob's<br>public key] --> J[Hash] --> K[Alice's sign] end D[Joe's<br>private key] H[Alice's<br>private key] L[Bob's<br>private key] Z --> F X --> J A -. Verify .-> G D -. Sign .-> G E -. Verify .-> K H -. Sign .-> K
To ensure the security and validity of each transaction, the private key is used to sign the next transaction, and the signature is verified using the corresponding public key. This process ensures that only the owner of the private key can authorize the transfer of bitcoins.
Each transaction is broadcast to the Bitcoin network, where it is verified by the network nodes. Once the transaction is confirmed, it is included in a block and added to the blockchain. The transaction is considered complete when it has been confirmed by a sufficient number of blocks, typically six or more.
Definitions
- A block is a collection of transactions that are grouped together within a certain timeframe.
- The blockchain is a linked list of all the blocks, a distributed ledger that contains all the transactions that have ever taken place since Bitcoin creation.
An acceptable block of transactions in the Bitcoin network is a block that has been confirmed by the network. Each block is composed of various components, including a SHA256 hash of the current block, an header containing the hash of the previous block, the root hash of the Merkle tree, the timestamp, and the nonce (a random number). Additionally, a block consists of a collection of transactions that are grouped together within a specific timeframe. These transactions are verified and added to the block, forming an integral part of the blockchain.
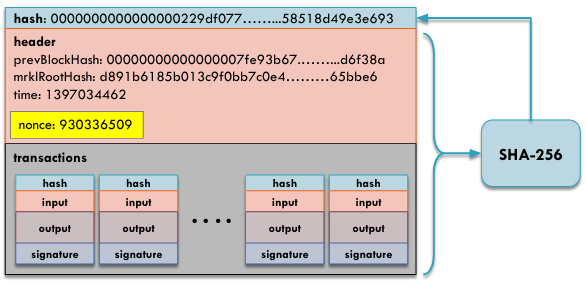
Bitcoin Mining
One of the fundamental and crucial aspects of Bitcoin is the mining process. Miners engage in a competitive race to generate a new valid block by solving a complex mathematical problem through brute force. The miner who successfully solves the problem is rewarded with a fixed number of BTC. Meanwhile, nodes play a vital role in validating the transactions that take place on the Bitcoin network.
- Miners carefully select the transactions that they want to include in the new block.
- Nodes thoroughly verify all the transactions within the block to ensure their validity.
- Once the transactions are verified, nodes propagate the new block to other nodes in the network.
To find the next block, miners must solve a challenging mathematical problem. The Bitcoin protocol dynamically adjusts the difficulty of this problem based on the number of miners participating in the network. On average, a new block is added to the Bitcoin blockchain approximately every 10 minutes. This process, known as Proof-of-Work, ensures the security and integrity of the Bitcoin network.
Definition
Proof-of-Work is a consensus algorithm that requires miners to solve a complex mathematical problem in order to add a new block to the blockchain. The difficulty of the problem is adjusted based on the number of miners competing against one another.
In the blockchain, when two miners simultaneously find a solution, it leads to a fork event. In such cases, the network selects the longest chain as the valid one. For a transaction to be confirmed, it must be included in a block that is at least 6/7 blocks away from the end of the chain. The longer the chain, the more computational power was expended in its construction.
Pseudo-Anonymity in Bitcoin Transactions
One of the defining characteristics of Bitcoin is its pseudo-anonymity when it comes to transactions. This means that individuals can have multiple anonymous addresses, and transactions made to oneself are virtually untraceable. Additionally, unlike traditional systems where authorities assign public and private keys, in Bitcoin, users generate their own keys, allowing for the creation of multiple identities.
However, it’s important to note that while the identities behind Bitcoin transactions remain anonymous, the transaction data itself is public and can be analyzed by anyone. For instance, if a transaction involves multiple inputs, it is highly likely that those inputs belong to the same entity. To protect the identity of the owner, shadow addresses are often used for change.
Definition
Shadow addresses are temporary addresses used to receive change from a transaction. They help maintain the privacy of the owner by preventing the linking of multiple transactions to a single address.
It’s worth mentioning that until 2013, a bug in the reference implementation made it possible to determine the shadow address with certainty. As a general rule, if a transaction has two outputs and one of them is new, it is likely to be the shadow address of the owner.
Bitlodine is a powerful tool developed in 2014 that enables the analysis of Bitcoin transactions and the identification of shadow addresses. With its capabilities, it becomes possible to track the flow of funds and uncover the origin of the coins. By thoroughly examining the blockchain, Bitlodine allows users to trace the movement of funds and identify the entities involved in these transactions. This tool proves to be invaluable in the field of cryptocurrency forensics, providing insights and evidence for investigations related to Bitcoin transactions.
Silk Road Investigation: Tracking Down the Dread Pirate Roberts
The Silk Road, a notorious dark web marketplace for illegal goods and services, was operated by an individual known as the “Dread Pirate Roberts.” This criminal enterprise came to an end when Ross William Ulbricht was indicted and convicted for his involvement in various Silk Road-related crimes, including narcotics trafficking conspiracy, computer hacking conspiracy, and money laundering conspiracy.
The investigation into the Silk Road and the identification of its operator involved meticulous digital forensics work. One breakthrough in the case came when Ulbricht used the nickname “altoid” on a forum to recruit developers for a project. This forum activity, combined with the use of his personal email address, provided a crucial link to connect Ulbricht to the Silk Road.
To trace Ulbricht’s activities on the Silk Road, investigators employed a technique known as blockchain analysis. They signed up on the marketplace, deposited a small amount of Bitcoin, and carefully noted the deposit address. However, tracking the flow of the coins proved challenging, as the Silk Road mixed them with thousands of others, making it difficult to follow the money trail. Despite this obstacle, investigators discovered a particular address that exhibited significant movement in 2012, indicating it may have been a shadow address associated with Ulbricht. This finding provided a valuable lead in the investigation.
Another breakthrough came from the same forum where Ulbricht used the “altoid” nickname. In a separate post, he sought assistance with a PHP code error and inadvertently included a Bitcoin address within the code. This address matched the one identified during the tracking process, confirming that both addresses were used by Ulbricht.
By piecing together these digital breadcrumbs, investigators were able to establish a strong connection between Ulbricht and the Silk Road. The combination of forum activity, email address usage, blockchain analysis, and code error provided the evidence needed to link Ulbricht to his illicit activities as the Dread Pirate Roberts.
The Silk Road investigation serves as a landmark case in the field of digital forensics, showcasing the power of blockchain analysis and meticulous investigative techniques in uncovering criminal activities conducted in the hidden corners of the internet.
Bitcoin usage as a ransomware payment
Bitcoin has emerged as a lucrative method for profiting from ransomware attacks. The initial wave of ransomware, known as Cryptolocker, made its debut on the internet at approximately 5 PM UTC on September 5th, 2013. This malicious software employed robust encryption to lock victims’ documents and demanded payment in Bitcoin for their decryption. The ransom initially started at 10 BTC but gradually decreased to 2 BTC, then 0.5 BTC, and finally 0.3 BTC. At the time, these amounts translated to significant sums of money, ranging from thousands to hundreds of euros.
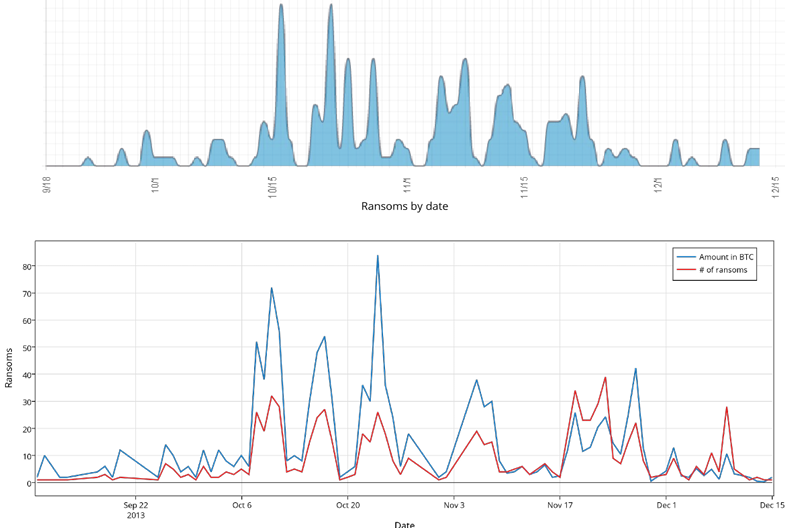
The graph clearly illustrates a correlation between the number of Bitcoin transactions and the spread of the Cryptolocker ransomware infections. As the number of infections increased, so did the number of Bitcoin transactions, indicating that victims were complying with the ransom demands and making payments to the attackers.
Challenges in Tracking Cryptocurrency Payments in Cybercrime
While Bitcoin is commonly associated with cybercrime, it is not the only cryptocurrency used by criminals. In fact, some lesser-known cryptocurrencies, such as Monero, offer stronger anonymity features compared to Bitcoin. This anonymity makes it attractive for cybercriminals, as they can convert their Bitcoin earnings into Monero to further obfuscate their tracks.
One notable example is the Wannacry ransomware operators, who utilized Monero to receive ransom payments from their victims. By using Monero, they were able to make it significantly more difficult for law enforcement agencies to trace the flow of funds and identify the individuals behind the attacks.
The use of alternative cryptocurrencies, or altcoins, in cybercrime is on the rise. These cryptocurrencies provide additional layers of privacy and security, making it challenging for investigators to track and trace illicit transactions. As a result, it becomes crucial for cybersecurity professionals and law enforcement agencies to develop effective methods and tools to monitor and analyze these alternative payment methods in order to combat cybercrime effectively.