Definition
A firewall is a network access control system that verifies all the packets flowing through it. Its main functions are:
- IP packet filtering (labeling each packet and decide whether it can pass)
- Network address translation (NAT)
A firewall serves as the primary control point between a protected network and external networks, acting as a security checkpoint. However, it is important to note that firewalls have limitations. They can only inspect and control the traffic that passes through them, making them ineffective against insider attacks unless the network is segmented. Additionally, firewalls are unable to monitor traffic that bypasses them through alternative channels, such as a separate modem or 5G connection connected to the same network.
The firewall itself is a computer and can have vulnerabilities that can be exploited. In most cases, firewalls are single-purpose machines with limited services and a smaller attack surface. However, a firewall is essentially a rule enforcer, and if the rules are not well-defined, it can provide inadequate protection. Firewall rules are the implementation of higher-level security policies, and a good practice is to build these policies on a default deny basis, creating a whitelist of allowed traffic. Firewalls can also be implemented within the operating system, such as Windows Firewall. It is crucial to have a firewall between malicious traffic and a server to ensure protection. From a high-level perspective, firewalls can be categorized based on their packet inspection capabilities and granularity of control.
The main distinction is between network and application layer firewalls:
- Network layer firewalls:
- Packet filters firewall (network), very simple and not implemented anymore because they are not secure
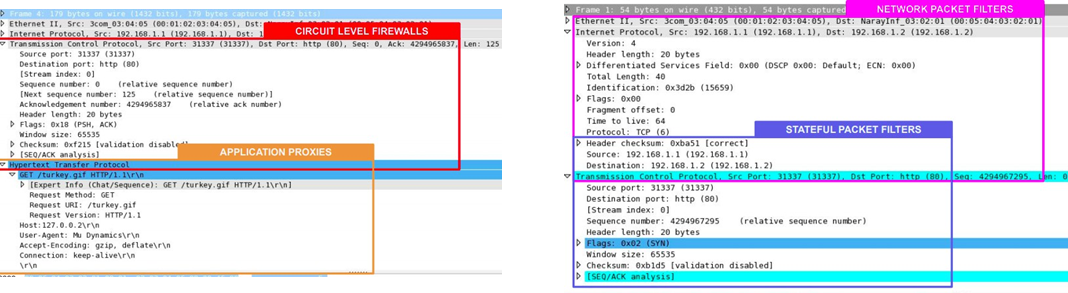
- Stateful packet filters firewall (network-transport), most common today and a standard in the industry
- Application layer firewalls:
- Circuit level firewalls (transport-application), don’t exist anymore
- Application Proxies (application)
These firewalls can analyze what passes through the network at different levels and depending on the firewall, different information can be analyzed, even the files someone is downloading.
Packet Filters Firewall
This kind of firewall consists of a packet-by-packet processing as independent entities, without considering the context. This makes it impossible to understand the relations between different packets and the concept of a session. As a consequence, these firewalls cannot track TCP connections (stateless) nor perform payload inspection, they can only analyze a single packet. If the malicious element is not contained in the single packet, it will not be detected. This firewall decodes the IP (and part of the TCP) header:
- source and destination IP
- source and destination port
- Protocol type
- IP options
No rules can be added concerning the network, transport, or application layer due to the fact that the firewall cannot analyze the payload, but only the header of the packet.
Some examples of rules are:
- Block any incoming packet (“default deny”),
iptables -P INPUT DROP #P = policy, always put in the firewall - Allow incoming packet if going to 10.0.0.1,
iptables -A INPUT -d 10.0.0.1 -j ALLOW, beginning of whitelist - Block anything out except SMTP (port 25),
iptables -P OUTPUT DROP, iptables -A OUTPUT –dport 25 -j ALLOW
With packets with spoofed IP, when a packet filter firewall is deployed, it depends on where the attacker is (if it is an internal address, the attacker will be blocked). If the attacker is external (e.g. smurfing), the firewall can block the request (block external requests with internal address). All firewalls basically allow to express these kinds of rules and, regardless of the specific syntax, every network packet filter allows to express the following concept: if (packet matches certain condition), do this, e.g. block, allow, log, etc.
Example of rules:
| Description | Firewall | SRC IP | SRC port | Direction | DEST IP | DEST port | Policy |
|---|---|---|---|---|---|---|---|
| Default deny | FW | all | any | all | all | any | deny |
| Allow internet access | FW | <src ip> | any | zone 1 → zone 2 | any | any | allow |
| Allow DNS | FW | <src ip> | any | zone 1 → zone 2 | <DNS server> | 53 | allow |
| Allow HTTP | FW | <src ip> | any | zone 1 → zone 2 | <web server> | 80 | allow |
| Allow HTTPS | FW | <src ip> | any | zone 1 → zone 2 | <web server> | 443 | allow |
| Allow SMTP | FW | <src ip> | any | zone 1 → zone 2 | <mail server> | 25 | allow |
| Allow FTP | FW | <src ip> | any | zone 1 → zone 2 | <FTP server> | 21 | allow |
| Allow SSH | FW | <src ip> | any | zone 1 → zone 2 | <SSH server> | 22 | allow |
| Allow connection to a specific IP | FW | <src ip> | any | zone 1 → zone 2 | <specific IP> | any | allow |
| Allow connection to a specific port | FW | <src ip> | any | zone 1 → zone 2 | any | <specific port> | allow |
Stateful (or Dynamic) Packet Filters
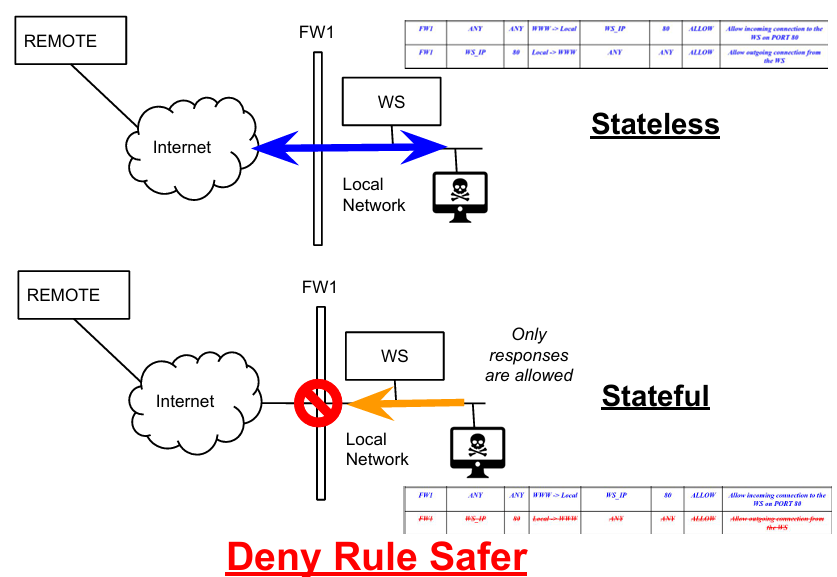
Packet filters have some additional functionalities that allow to track the connection and the TCP state machine, together with the relation between packets. They keep track of the TCP state machine, after SYN signal, SYN-ACK must follow, and to track connections without adding a response rule and make deny rule safer. This has huge impacts on how rules are written: since the connection is tracked, there is no need to implement a rule to allow the response. Also, deny rule is safer because less things are allowed, an internal attacker can not exfiltrate information, because there is no move from internal to external (response rule).
The main issue is that, while stateless’ main characteristics is the number of packets per second they can analyzed, in this case performance is bounded on a per-connection basis, not on a per-packet basis.
The number of simultaneous connections is just as important as packets per second. To store information a cache is needed within the firewall: the more connection, the more memory is occupied, the more time is required to analyze them. Moreover, an attacker can fill the memory until the firewall won’t work (DoS). This firewall is however very common: they have better expressiveness and allow tracking (logging and accounting on) connections. Moreover, a deeper content inspection can be performed, since connection can be tracked: reconstruction of application-layer protocols and application-layer filtering, defragmented packets’ management. Finally, it is possible to perform Network Address Translation (NAT) between internal and external networks.
Stateful packet filters allow session handling. A session is an atomic, transport-layer exchange of application data between 2 hosts. The main transport protocols are TCP (Transmission Control Protocol, where session = TCP connection) and UDP (User Datagram Protocol, where session concept does not exist, connectionless). Session-handling is fundamental for NAT, session is emulated in UDP case in fact. Being UDP widely used, we can’t dismiss it (e.g. DNS, VoIP H.323, video streaming, etc) so it must be managed. It is however difficult to secure and handle, because it is connectionless.
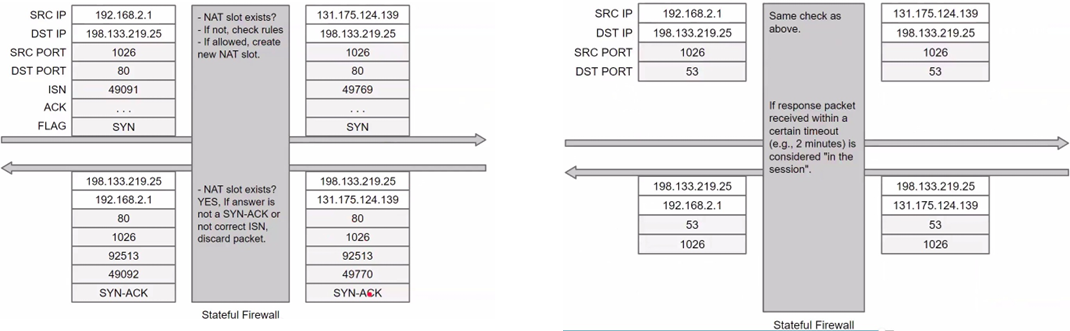
The concept of “session” is thus emulated and to have a similar functionality to TCP the basic functionality is receiving a response every time a packet is sent. A timeout can be added after a packet is sent, whatever returns is accepted. The problem here is that the attacker might generate a packet and brute force the port number within the timeout. Another issue is related to dynamic protocols (e.g., DCC, RDT, instant messengers, file transfer) which transmit network information data (e.g., port) at application layer.
For instance, FTP uses dynamic connections allocated for file uploads, downloads, output of commands. The client will try to connect to the server with port application command, the server will then proceed sending the file. Stateful firewalls must manage such dynamic protocols. Data transfer could be blocked by firewalls because of the static definition of rules: if source and destination ports are dynamic (exchanged in the message) the stateful firewall must also analyze the content and map the connection.
To establish a connection with dynamic protocol, the client-side firewall must open port 21 outbound, dynamically open/close the (inbound) ports that the client specifies in the command. On the server-side the firewall must open port 21 inbound, dynamically open/close the (outbound) ports that the client specifies in the command. Besides, another modality (passive mode) uses pasv command so that connection is initiated by the client. Still the firewall will have to dynamically open/close the ports.
Deep inspection and intrusions modern firewalls can analyze packets and sessions even more in depth, e.g. recognize MIME multipart attachments in SMTP flows and send data to antiviruses, recognize a set of “known attack packets” patterns to be blocked (IPS, Intrusion Prevention Systems), however they can have update problems and cannot recognize zero-day attacks (only known ones).
Circuit Firewalls (Legacy)
Circuit firewalls, which used to exist in the past, operated by relaying TCP connections. In this setup, the client would connect to a specific TCP port on the firewall, which would then establish a connection to the desired server using the specified address and port.
Unlike other types of firewalls, circuit firewalls were not transparent to the client and required the use of different proxies based on the protocol being protected. Managing circuit firewalls was more challenging due to the need for specific proxies and the lack of transparency for clients. However, circuit firewalls are no longer in use today, as advancements in firewall technology have led to the development of more efficient and effective alternatives.
Application Proxies
Application proxies firewalls operate at the application layer and provide an additional layer of security for network traffic. Unlike circuit firewalls, they are not transparent to clients and require specific proxy servers for each protocol. One of their key advantages is the ability to inspect, validate, and manipulate application data, such as rewriting HTTP frames. This allows them to perform tasks like user authentication, filtering policies, advanced logging, and content filtering or scanning, including antivirus and spam detection (although limited to unencrypted HTTP connections).
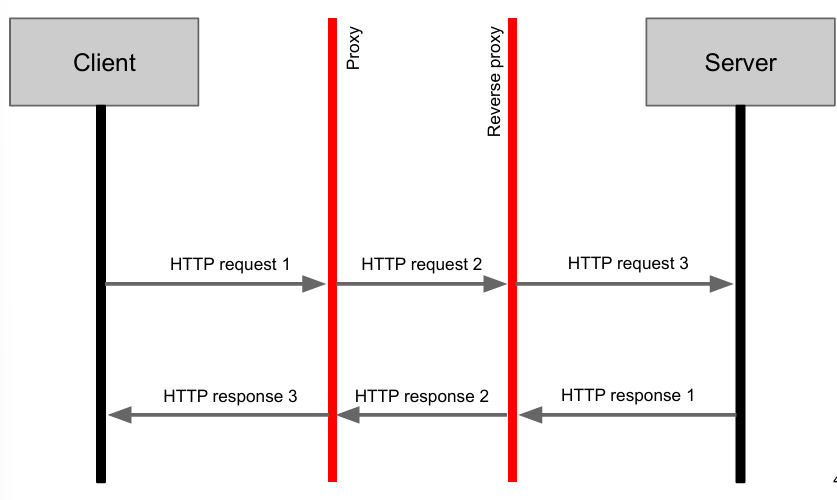
Application proxies can also be used as reverse proxies to protect servers from web attacks like SQL injection and cross-site scripting (XSS). By validating the output sent from the client to the server, they help prevent malicious code from reaching the server. These firewalls are typically implemented on commercial off-the-shelf operating systems (COTS OSs).
While application proxies offer enhanced security and control at the application layer, they do come with some trade-offs. They require specific proxy servers for each protocol, which can increase complexity and maintenance overhead. Additionally, their effectiveness may be limited to non-encrypted connections, as they rely on inspecting and manipulating the application data. Nonetheless, application proxies remain a valuable tool in defending against various application-layer threats and ensuring the integrity and security of network traffic.
Architectures for secure networks
Dual- or Multi-zone Architectures
In most cases, the perimeter defense works on the assumption that what is “good” is inside, and what’s outside should be kept outside if possible: this is the castle approach. However, there are two counter examples: the access to resources from remote (i.e., to a web server, to FTP, mail transfer) and from remote users to the corporate network. This approach is not always valid in real world. However, if we mix externally accessible servers with internal clients, we lower the security of the internal network, because internal network is exposed to external access (attackers).
Solution
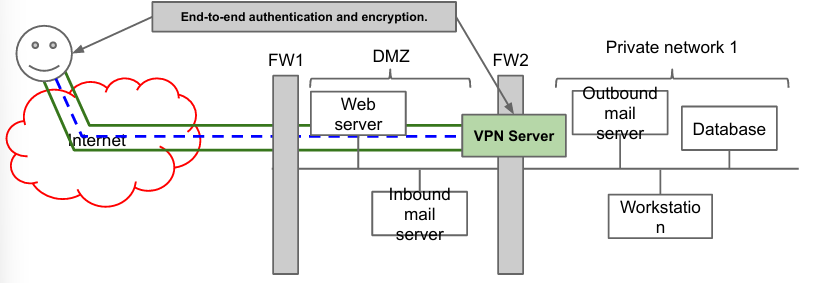
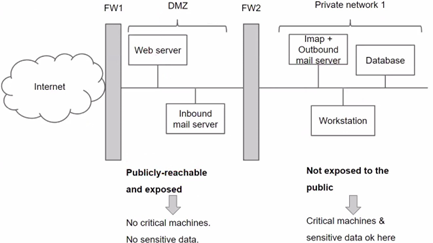
The solution consists of allowing external access to the accessible servers, but not to the internal network, i.e. splitting the network by privileges levels. Firewalls can be used to regulate access. In practice, we create a semi-public zone called DMZ (demilitarized zone).
The DMZ will host public servers (web, FTP, public DNS server, intake SMTP) exposed to clients nothing critical nor sensitive. The DMZ is almost as risky as the Internet.
This is not the only solution: if the database is more critical, another zone with another firewall can be created between database and workstation. If there is no firewall between two connected sections, no additional rule is required to allow them to communicate.
Virtual Private Networks - VPNs
Definition
A VPN (Virtual Private Network) is a secure, encrypted connection between two networks or between a remote user and a network. It allows users to access resources on a private network from a remote location.
To enable remote workers to access the same resources as if they were in the office, Virtual Private Networks (VPNs) were developed. VPNs allow employees to securely connect to the private zone and establish connections between remote sites without the need for dedicated lines. By encrypting the data transmitted over a public network, such as the Internet, VPNs ensure the confidentiality, integrity, and availability of the transmitted data. Essentially, a VPN creates an encrypted overlay connection that mimics the path followed by packets transmitted from the office, allowing firewalls and restrictions to function in the same way for remote users.
There are two VPN Modes:
- Full tunneling: every packet goes through the tunnel independently of its final direction. This method is more secure, as all traffic is filtered and validated as if the client were in the corporate network. However, it can be inefficient and resource-intensive due to the traffic multiplication. To manage this, a single point of control and application of all security policies is applied.
- Split tunneling: only the traffic directed to the private zone is tunneled into the VPN. Traffic to the corporate network is sent through the VPN, while traffic to the Internet is sent directly to the ISP. This method is more efficient and less resource-intensive, but it is less secure as browser navigation is not always checked. Split tunneling is similar to the case of a PC connected via a 4G modem to the Internet.
Some VPN technologies are:
- PPTP (Point-to-point Tunnelling Protocol): proprietary Microsoft protocol, variant of PPP with authentication and cryptography
- VPN over SSL, SSH tunnel, or OpenVPN.net (open source)
- IPSEC: security extensions of IPv6, backported to IPv4, authentication and cryptography at IP layer