Networking is a complex system that consists of various physical devices and topologies. To ensure efficient communication, a layered approach is employed. Each layer within this framework is associated with specific protocols and, as packets traverse through these layers, they are encapsulated; each layer is provided with instructions on how to interpret the content of the packet. It is crucial to understand the concept of addressing in networking. Hosts are uniquely identified by addresses, and each layer has its own addressing structure, such as MAC address at the data link layer, IP address at the internet layer, and port at the transport layer.
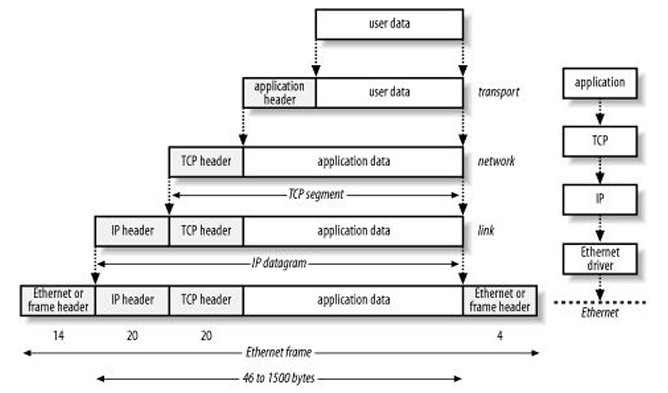
Transport protocols
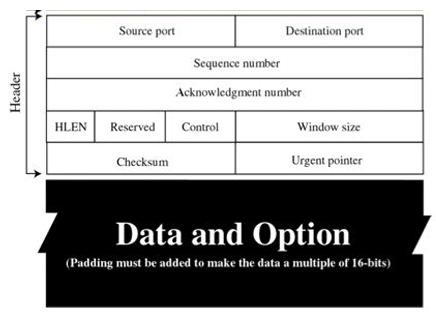
A connection-oriented protocol is a protocol that requires the establishment of a connection before data is transmitted and ensures that the data is delivered correctly. TCP is an example of a connection-oriented protocol.
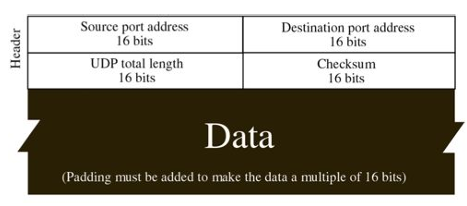
A connectionless protocol is a protocol that does not require the establishment of a connection before data is transmitted and does not guarantee the delivery of data. UDP is an example of a connectionless protocol.
Typical network attacks can be classified into three categories based on the security properties they violate:
- Denial of Service (against availability): service unavailable to legitimate users (can be distributed or not)
- Sniffng (against confidentiality): abusive reading of network packets
- Spoofing (against integrity and authenticity): forging network packets
Denial of Service
Definition
A denial-of-service (DoS) attack is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the Internet.
These attacks include killer packets, SYN flood, smurf, multiplication or amplification attacks and disturbed DoS. Killer packet attacks exploit vulnerabilities in the protocol to make a communication fail: the receiver expects a well formed pack but received a killer (unexpected/malformed) one. The other attacks make service unavailable by exhausting the service’s resources. The goal is always to make the service unavailable so that user can not connect to it.
Killer Packets
Killer packets exploit vulnerabilities in the protocol to make a communication fail.
-
The Ping of Death consists of a pathological ICMP echo request that exploits a memory error in the protocol implementation. The attacker sends a ping packet that exceeds the maximum length allowed by the protocol, causing the receiver to crash. This attack is not successful anymore because machines now accept different dimensions of payload.
ICMP (Internet Control Message Protocol) is used to send debugging information and error reports between hosts, routers and other network devices at IP level. ICMP messages can be requests, responses, error messages, among which there is a message called echo request/reply, used to test connectivity (
ping).pingcommand sends an ICMP with a particular dimension request and asks for a ICMP response of the same dimension (max 64 kB, usually much less).Machines can be crashed by sending IP packets that exceed maximum legal length (65535 octets):
ping -l 65527(win) orping -s 65527(*NIX), being the payload greater than the expected ones. At the time it was discovered, the system could not handle the dimension and crashed because, on the receiver’s side, buffer overflow happened, even from remote. Nowadays, machines accept different dimensions of payload, so this attack is not really successful. -
The Teardrop attack exploits vulnerabilities in the TCP reassembly. TCP fragments packets that are too big to be exchanged, and the packets are structured like a linked list. The attacker sends packets with overlapping offsets, causing the kernel to hang or crash.
Packets are structured like a linked list (header specifies the offset of the next fragment) so that the receiver has the instructions to reassemble the packet. However, packets with overlapping offsets were nor managed correctly: it was possible to make packets so that while reassembling kernel could hang/crash.
Teardrop attack was first discovered in 1997 on all OSs and then patched, it came back in 2009 with windows vista because between 1997 and 2009 OSs changed, the protocol was the same and this vulnerability came back.
-
The Land attack exploits a vulnerability in the TCP/IP stack by sending packets with the source IP equal to the destination IP and the SYN flag set. This causes the packet to loop in the protocol stack of the first machine, exhausting its resources. This happened because the case
source IP = dest IPhad not been managed. The same happened with SP2 in Windows XP.
Flooding
Definition
A flooding attack is a type of DoS attack in which the attacker sends a large number of packets to a target with the aim of consuming the target’s resources and making it unavailable to legitimate users.
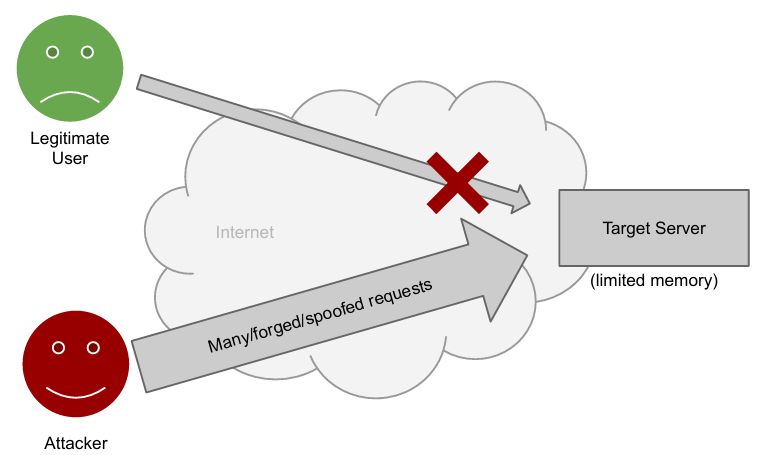
A large number of packets are generated until the resources of the target server are depleted. Since the target server has limited resources, this type of attack is always possible. There is no definitive solution to completely eliminate these attacks. However, the system can be designed in a clever way to handle an average attack by assessing the threat and evaluating the load. To mitigate this, it is important to avoid providing shortcuts that make flooding easier, thus requiring the attacker to use the same amount of resources on their machine as they want to exploit on the target machine. This is the main focus of most mitigations for this type of attack, where the target takes action while the attacker does not.
SYN Flood Attack: TCP/IP three way handshake
Definition
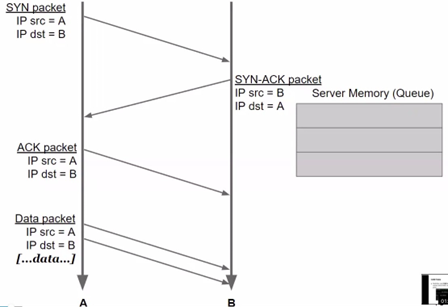
SYN packets are used to initiate a connection between two hosts. The three-way handshake is a method used in a TCP/IP network to create a connection between a local host/client and a server. It is a three-step method that requires both the client and server to exchange SYN and ACK (acknowledgment) packets before actual data communication begins.
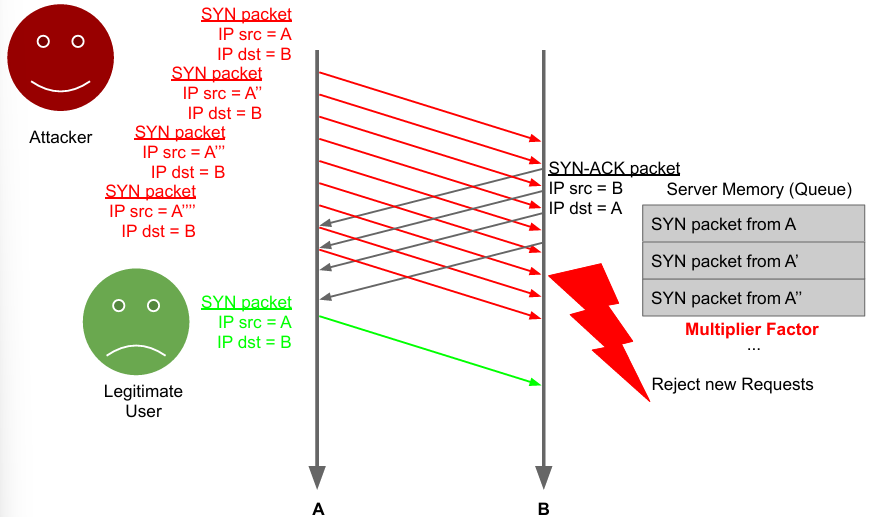
In this case, the multiplier factor is the fact that every time the server receives a SYN packet it has to save it in memory (which is limited): an attacker simply send packets, without having to store them, needing less resources. An attacker just has to send a high volume of SYN requests with spoofed source address (faking the source, aka using different IPs), many TCP/IP connections fill the queue and the service will not be able to answer anymore.
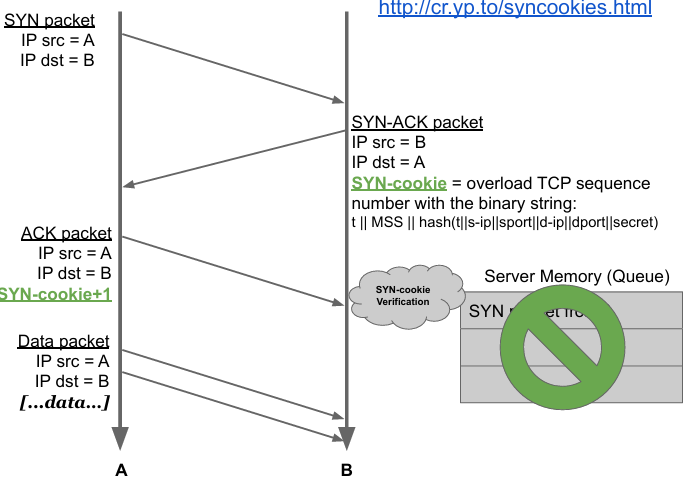
This attack can be mitigated by removing the multiplier factor (memory) using SYN cookies. SYN cookies are just tokens that allow to reply with SYN+ACK but discard the half-open connection and wait for a subsequent ACK. Instead of storing all received packets, when receiving one, the target generates a SYN cookie (sync number) which is sent to the sender entity. The receiver entity will now wait for a valid SYN cookie without storing anything. To complete the connection, the attacker has to send a valid SYN cookie. The server has to just compute the SYN cookies, which is less intensive than storing everything.
Distributed DoS
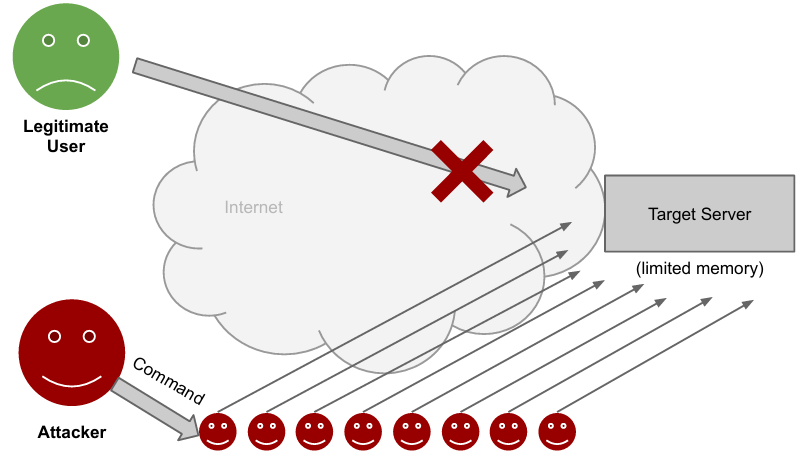
In distributed DoS, the attacker has control of a network of compromised computers (zombies/botnet) controlled by the command and control server under the direct control of the attacker. All zombies will flood the target server with requests. It is evident that there is no real solution to this problem, as the multiplier factor is the computational resource of the botnet. The difference here is that the target has no control over this multiplier factor, as it is external. The botnet can have any size the attacker desires, making it a powerful tool for the attacker. The only way to eliminate this threat is to track the botnet and disarm it.
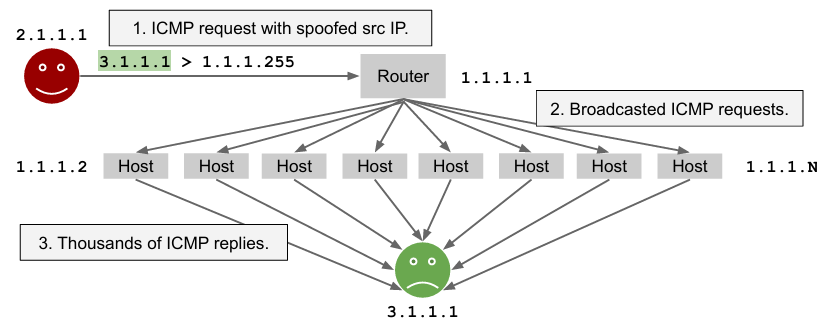
The Smurf attack is an example of a DDoS attack. The attacker sends ICMP packets with a spoofed sender (victim) to a broadcast address. This attack is no longer possible, as requests from external networks are now blocked. However, if the attacker is inside the network, the attack can still be executed. The amplifier factor in this attack is the size of the network. Each host inside the network will receive an ICMP request, generating ICMP replies directed at the victim and flooding the target. This type of attack is also known as amplification-based attacks. Another way to execute DoS attacks is by exploiting protocols where the size of the response is larger than that of the request, creating an amplification effect.
Network level sniffing
Normally, a network interface card (NIC) only intercepts and passes packets directed to the host’s IP to the operating system. However, in promiscuous mode, the NIC will pass all packets read off the wire to the OS. Attackers can exploit this by putting their NIC in promiscuous mode, allowing them to intercept all packets transmitted along the wire.
To mitigate sniffing attacks, it is recommended to use switched networks instead of hub-based networks. Unlike hubs, switches selectively relay traffic to the corresponding NIC based on ARP, ensuring that messages are directly related to the intended receiver’s NIC.
ARP Spoofing
Definition
ARP (Address Resolution Protocol) is a protocol used to map an IP address to a MAC address. It is used to resolve IP addresses to MAC addresses, allowing devices to communicate with each other on a local network.
ARP maps 32 bits IPv4 addresses to 48 bits hardware or MAC addresses. To send the message the receiver’s MAC must be known, otherwise ARP is necessary. However, an attacker can forge replies easily due to the lack of authentication, the first that answers the ARP request is the one accepted. If the first one is the attacker it will be accepted (instead of the legitimate user’s answer).
Each host caches the replies (arp -a) so each of them can forge the reply. This attack is called ARP Spoofing (or Cache Poisoning). If ARP is updating with the wrong address, it is updating on all hosts of the network. This attack is very successful because all packets will be redirected to the attacker’s desired MAC. The first answer (the attacker’s) can be malicious: the traffic might go to the attacker first (sniffing), they will analyze all packets.
Another possibility is generating DoS: if the gateway of the network (from external to internal network) is spoofed by the attacker, all the traffic will reach the address decided by the attacker instead of the gateway’s. This is a DoS attack in the network.
arp -d 15.1.1.1 # clear the record for 15.1.1.1
ping -n 1 15.1.1.1 # try to reach 15.1.1.1 (ping with 32b)
reply from 15.1.1.1 bytes-32 time<10ms TTL-225 # the ARP layer has resolved the MAC address
arp -a # clear arp cache
Interface # legitimate arp cache
15.1.1.1 physical address 1 dynamic
15.1.1.25 physical address 2 dynamicThe attacker can create a script to flood the network and tell every host that 15.1.1.1 is at the attacker’s NIC, and this is how poisoning happens. Now, when checking the ARP cache, 15.1.1.1’s physical address is the poisoned one. It is not possible to be sure about the IP and MAC addresses of the attacker (both can be spoofed). The traffic is now redirected to the poisoned physical address.
Mitigations against this attack include hardcoded IP addresses, which cannot be spoofed or detect whether the same MAC address belongs to different IP addresses: this is an anomaly that can be detected, only after the attack happens. Alternatively, to prevent this attack, we can wait for some ARP request and check for conflicts before storing the addresses in the cache: the legitimate user will answer for sure, the point is who answers first. Also, ID can be added to the requests, so that only certain requests with a certain ID are accepted, however the ID can be guessed (even if IDs make attacks harder). In this case the attacker must be on the same network of the victim.
MAC flooding
In switch-based networks, MAC flooding attacks may fail due to the use of CAM tables (caches) by switches. CAM tables help identify which MAC addresses are connected to which ports. While CAM tables mitigate sniffing, they have limited space as they are caches.
However, an attacker can flood the CAM table by generating a large number of ARP replies. Tools like Dsniff can generate approximately 155k spoofed packets per minute, quickly filling up the CAM table. When the CAM table is full, ARP replies cannot be cached, and all packets must be forwarded to every port, similar to how hubs operate. This prevents DoS and keeps the service available.
It's important to note that this attack does not cause a true DoS but rather turns switch-based networks into hub-based networks.
One mitigation against these attacks is to implement port security, which limits the number of devices that can connect to each port making flooding attacks impossible, especially when differentiating between client and gateway ports. However, ARP spoofing can still be possible in switch-based networks.
Spanning Tree Protocol
STP (Spanning Tree Protocol) is used to prevent loops in a switched network by creating a spanning tree. Switches communicate with each other by exchanging BPDU (Bridge Protocol Data Unit) packets to determine the root node of the tree.
BPDU packets do not have any authentication mechanism, which makes them vulnerable to attacks.
Attackers can exploit the lack of authentication in BPDU packets for various purposes, such as sniffing network traffic or performing ARP spoofing attacks. Since BPDU packets are network-level protocols, they prioritize performance over security, which leaves them susceptible to manipulation by malicious actors.
It is crucial to implement additional security measures to protect against these attacks. This may include implementing authentication mechanisms for BPDU packets or using other security protocols to ensure the integrity and confidentiality of network communications. By enhancing the security of the network infrastructure, organizations can mitigate the risks associated with unauthorized manipulation of the spanning tree and protect the confidentiality and integrity of their network traffic.
IP address Spoofing (UDO/ICMP)
Spoofing IP addresses is easy, because IP source addresses are not authenticated. Also changing it in UDP or ICMP packets is easy. However, the attacker will not see their answers (e.g. because they are on a different network), because they will be sent to the spoofed host (blind spoofing): only the victim will receive the responses. But if the attacker is on the same network, they can sniff the rest or exploit ARP spoofing, the attacker will also see the responses.
For TCP it is not so easy: to establish a connection with TCP a 3 way handshake must be completed, TCP uses sequence numbers for reordering and acknowledging packets. A semi-random Initial Sequence Number (ISN) is chosen and embedded, to establish a connections random ISN must be chosen so that 3 way handshake can be completed.
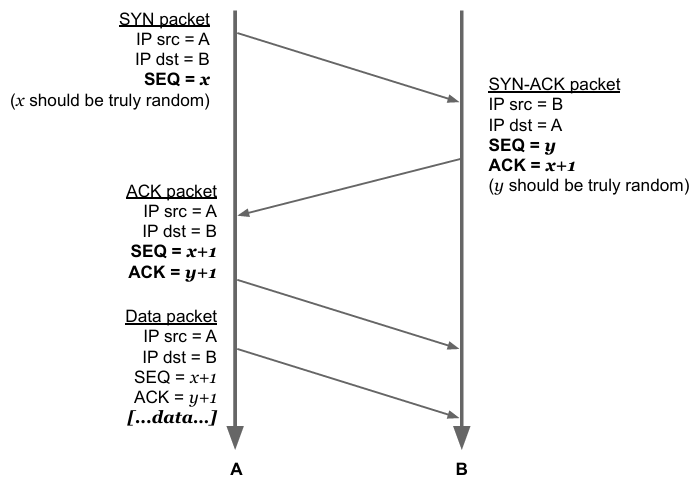
Considering the 3 way handshake: in case of blind spoofing, to spoof
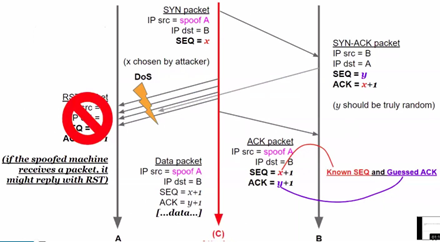
The attacker must guess the SEQ number and prevent rst package. To preventing
In 1995 it was easy to guess ISNs due to easy TCP implementations (Kevin Mitnick). ISN distribution in different systems can be analyzed. The worst distribution is the one chosen by IRIX, in which is easy to know what the next ISN will be. Value distribution can be assessed in terms of how spread out they are and how many they are: if there is a pattern in the distribution, it will be way easier to guess ISN. Also points whose distribution is dense but numerous are easier to guess (being many it is still way harder than previous cases). However, if the attacker is in the same network of the victim it is way easier to sniff all packets that are being exchanged, nothing should be guessed. It is enough to DoS one of the entities so that they cannot receive or sand any more packets.
To take over an active TCP session from the same network the attacker follows the conversation between
This attack allows to control/resync all the traffic flowing through.
Definition
The man in the middle attack is a wide category of attacks in which the attacker can impersonate the server with respect to the client and vice-versa. It can be either physical (the attacker is e.g. on the firewall on a network) or logical (the attacker fakes a gateway) and full or half duplex.
flowchart LR subgraph Half_Duplex H1V[[Host 1 - Victim]] H2V[[Host 2 - Victim]] H3A[[Host 3 - Attacker]] H1V --> H3A --> H2V --> H1V end subgraph Full_Duplex H1V1[[Host 1 - Victim]] H2V1[[Host 2 - Victim]] H3A1[[Host 3 - Attacker]] H1V1 --> H3A1 --> H2V1 --> H3A1 --> H1V1 end
Communication between entities is entirely under the attacker’s control. If the attacker is able to ARP spoof the gateway of a LAN they become a logical man in the middle.
DNS cache poisoning attacks
MAC addresses are related to hardware, while IPs are related to networks. These addresses are hard to remember for humans: in fact this is DNSs’ job (Domain Name System). It is required that a naming system is as short as possible, easy to memorize, unique, customizable and it should reflect organizational structure, while quickly translating to and from existing computer friendly addressing systems.
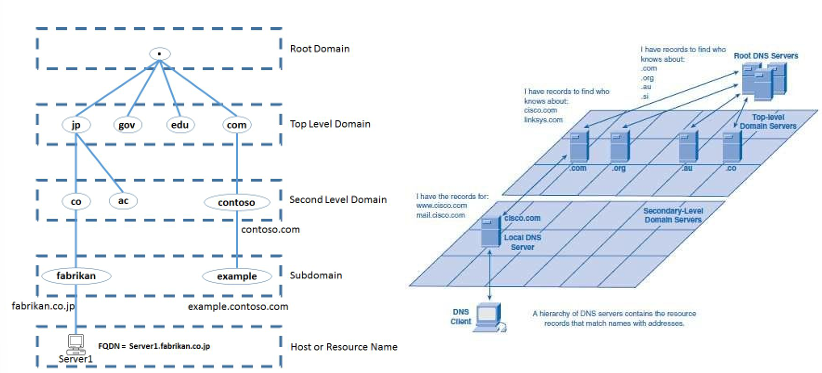
DNS exploits a distributed database organized as a hierarchy of servers that provide the mappings. Each server keeps a small cache of the mappings. It is based on UDP (Port 53) and messages are not authenticated, there is a weak auth form. When a domain name is used/requested and isn’t in the local cache, the system queries a DNS server, the hierarchy that contains the resources records to match domain name and IP is followed until the owner is reached.
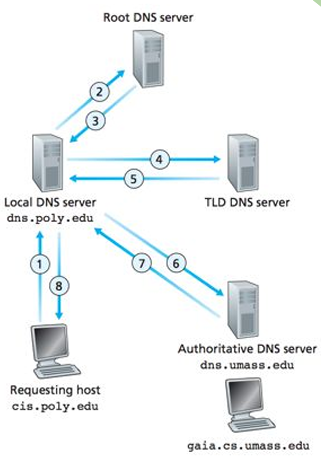
When a non authoritative DNS server receives a request to resolve a domain name, if the answer is cached it answers, otherwise it can resolve the name on behalf of the client (recursive mode) or give the authoritative DNS address (iterative mode).
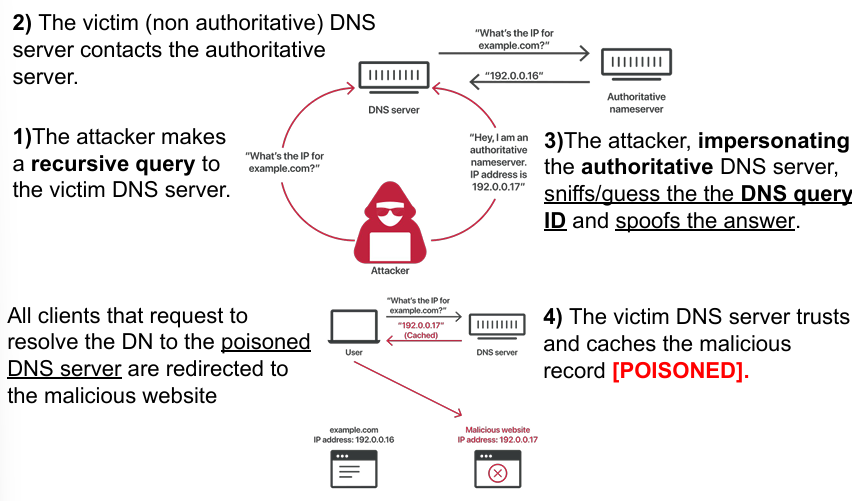
In these attacks, the attacker knows that there is non authoritative DNS server in the network (e.g. local). They will first make a recursive query to the victim’s DNS server, asking for something’s IP address. The non authoritative DNS will contact the authoritative one which will try to answer the DNS server. The attacker will now impersonate the authoritative DNS server and sniff/guess the DNS query ID spoofing the answer. To conclude the attack, the attacker has to guess the query ID, this issue is similar to guessing ISN. At this point the victim’s DNS serve trusts and caches the malicious records (poisoned). All clients that request to resolve the domain name to the poisoned DNS server are redirected to the malicious website. ID of DNS can be sniffed by brute forcing for example.
Dynamic Host Configuration Protocol - DHCP Poisoning Attacks
Definition
DHCP (Dynamic Host Configuration Protocol) is a network management protocol used on IP networks where a DHCP server dynamically assigns an IP address and other network configuration parameters to each device on a network so they can communicate with other IP networks. A DHCP server enables computers to request IP addresses and networking parameters automatically.
It allows network admins to supervise and distribute configuration parameters for network hosts from a central point. However, DHCP is not authenticated: being the first connection it is not possible to authenticate.
- When DHCP server is unavailable, the client is unable to access enterprises network.
- When a new host connects, it will send a DCHP discover and select a received DHCP offer.
- When connection ends, the client releases the IP address.
Being an unauthenticated protocol, the attacker can intercept the DHCP request and be the first to answer: the client will believe its answer. With a spoofed DHCP response, the attacker can set IP address, DNS addresses and the default gateway of the victim client. This attack is even simpler: the attacker will be able to change anything in the host. ICMP can also inform the hosts about better routes/gateways (redirect function).
Routers are responsible for keeping routing information up to date and are assumed to discover best routes for every destination. Hosts begin with minimal routing information and learn new routes from routers. A host may boot up knowing the address of one router only bit that may not be the best route. When a router detects a host using a non optimal route it sends and ICMP redirect message to the host and forwards the message. The host is expected to then update its routing table.
In this attack the attacker can forge a spoofed ICMP redirect packet to re-route traffic on specific routes or to a specific host that may be not a router at all. The attack can be used to hijack traffic or perform DoS attacks. It is weakly authenticated: an ICMP message includes the IP header and a portion of the payload (usually the first 8b) of the original IP datagram. Authentication is weak, because it is abused on something not secret: the attacker needs to intercept a packet in the original connection to forge the reply. In this way, they create a half duplex MITM situation. Also, handling ICMP redirect is OS dependent.
In general the attacker can announce routes to a router, they can play a lot of tricks:
By re-routing and adding steps so that communication follows a longer path communication is hijacked and sniffed, for example by re-routing toward a node under the attacker’s control.