There is a strong difference between identification and authentication and it is important to understand it before diving into the topic.
Definitions
- Identification is the process of declaring an identifier, like a name, a number, or a code.
- Authentication is the process of providing a proof that verifies the identity of the entity.
This means that, identification is the process of declaring who you are, while authentication is the process of proving who you are, so from the identification process, you can have multiple authentications. The authentication process can be unidirectional or bidirectional.
- In a unidirectional authentication system, an entity declares its identifier and a proof of that to another entity.
- In a bidirectional authentication system, both entities provide a proof of their identity to each other. This is like two unidirectional authentication systems happening at the same time.
sequenceDiagram Entity1 ->> Entity2: "I'm Entity 1" Entity1 ->> Entity2: "Proof me that I'm Entity 1" Entity2 ->> Entity1: "I'm Entity 2" Entity2 ->> Entity1: "Proof me that I'm Entity 2"
The authentication process may involve multiple entities, like a human, a computer, or a network and the process may rely on one or more of the following factors:
- Something that the entity knows (something to know): like a password, a PIN, or a secret handshake.
- Something that the entity has (something to have): like a door key, a smart card, or a token.
- Something that the entity is (something to be): like a face, a voice, or fingerprints.
The authentication between humans uses more the “to be” factor than the “to have” or the “to know” factors, while the authentication between machines uses more the “to know” factor than the “to have” or the “to be” factors. In fact, people are used to recognize each other by their faces, voices, or fingerprints, than by the things they have or the things they know. On the other hand, machines are used to recognize each other by the things they know, like passwords or keys, than by the things they have/are. All the three factors can be used in a multi-factor authentication system, where two or three factors are used together to authenticate an entity.
Something to know - Passwords and PINs
The “to know” factor is the most common authentication factor used in computer systems. It is based on something that the entity knows, like a password, a PIN, or a secret handshake. The advantages of this factor are the low cost, the ease of deployment, and the low technical barrier. The disadvantages are that the secrets can be stolen or snooped, guessed, or cracked.
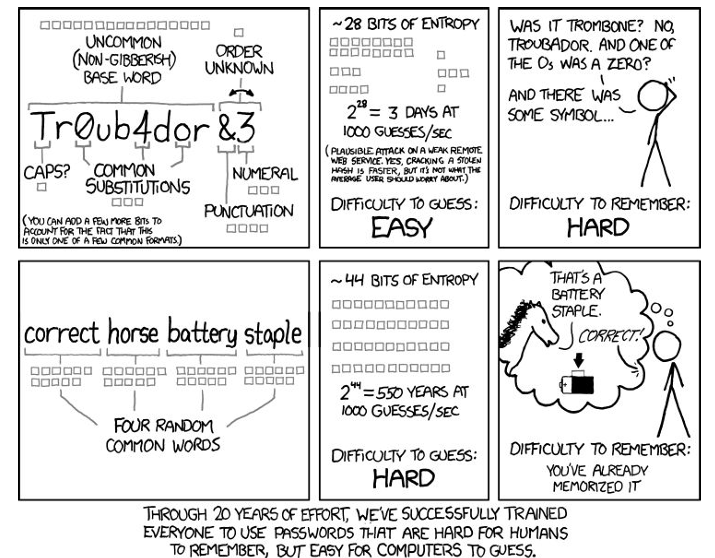
To mitigate these disadvantages, it is important to enforce passwords that change or expire frequently, that are long and have a rich character set, and that are not related to the user. These countermeasures can help to protect the passwords, but have also indirect costs, like the usability of the system. Users are inherently unable to keep secrets, unable to remember complex passwords, and unable to pick unlimited countermeasures. To choose the right countermeasures, it is important to evaluate the most likely attack in the scenario and choose the countermeasures that are worth asking users to adhere to.
- Against snooping, it is important to change the password frequently, while the complexity and not being related to the user are less important.
- Against guessing, it is important to have a password that’s not related to the user, while the complexity and the change may only help.
- Against cracking, it is important to have a long and rich password, while the frequently change and the not being related to the user may help.
| Attack | Description | Countermeasures |
|---|---|---|
| Snooping | The attacker listens to the communication between the entities | Change the password frequently |
| Guessing | The attacker tries to guess the password | Use a password that’s not related to the user |
| Cracking | The attacker tries to crack the password | Use a long and rich password |
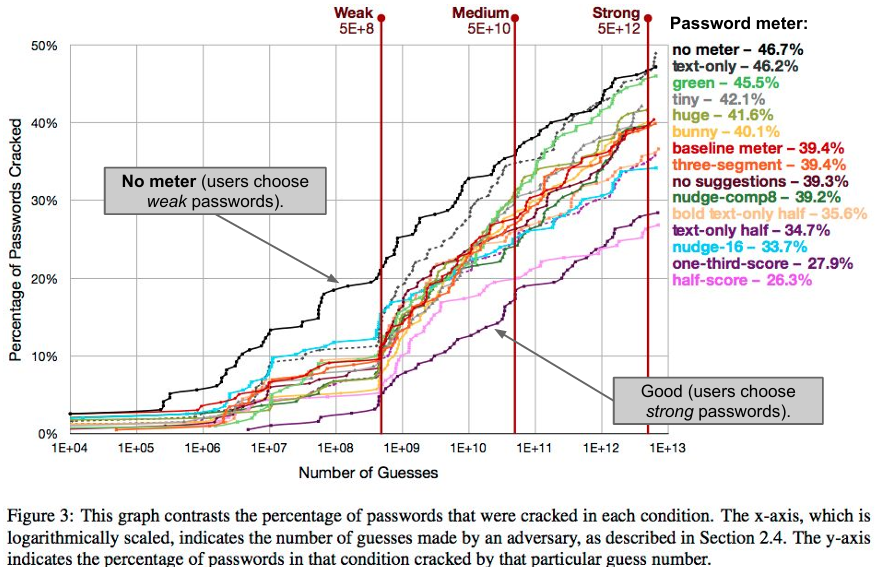
The user must be educated about the importance of security and the complexity of passwords, enforcing strong passwords in the process and expiring or changing them frequently. The password complexity must be enforced by the system, by requiring a rich character set, mixed case, and long enough password. In order to help the users to create a strong password, the system can use password meters to balance the usability of the system, showing if there are enough characters, if the password is long enough, or if it has a rich character set.
When we talk about secure password exchange, we are talking about the process of sharing a secret between two entities (like what happens in symmetric encryption). To minimize the risk that secrets get stolen, it is important to use mutual authentication if possible, to use a challenge-response scheme, and to use random data to avoid replay attacks.
sequenceDiagram Entity1 ->> Entity2: "My identifier is 'Entity 1'. Let me authenticate." Note over Entity1,Entity2: Challenge Computation Entity2 ->> Entity1: "Compute hash(<this random data> + <secret>)" + "<this random data>" Note over Entity2,Entity1: Hash verification Entity1 ->> Entity2: hash(<this random data> + <secret>) Note over Entity2,Entity1: Challenge Computation Entity1 ->> Entity2: "Compute hash(<this random data> + <secret> + <other random data>)" + "<other random data>" Note over Entity1,Entity2: Hash verification Entity2 ->> Entity1: hash(<this random data> + <secret> + <other random data>)
To secure the password storage, never store passwords in clear, to use cryptographic protection, to enforce access control policies, and to never disclose secrets in password-recovery schemes.
Something to have - Tokens, Smart Cards, and Smart Phones
The “to have” factor is based on something that the entity possesses, like a token, a smart card, or a smart phone. The advantages of this factor are the human factor (less likely to hand out a key), the relatively low cost, and the good level of security. The disadvantages are that it can be hard to deploy and that it can be lost or stolen. The fact that they can be lost or stolen can be mitigated by using them with a second factor (like a password).
Example of classic technologies that use the “to have” factor are:
-
one-time password generators: devices with a secret key and a counter synchronized with the host, that generate a one-time password every 30-60 seconds. The client computes a MAC using the counter and the key, and the host verifies the MAC using the counter and the key. This method is used in online banking, admin consoles, and credit cards.
The one-time password generators evolve from a static OTP list, used by banks and other services to provide a second factor of authentication. The static OTP list is known to both the client and the host, and the host chooses a challenge that the client must respond to using the OTP list. Modern versions of the one-time password generators are software that implements the same functionality of the hardware devices.
The key difference is that the hardware devices are closed, embedded systems, while the software apps work on general-purpose software and hardware platforms that can be infected by malicious apps.
-
smart cards: devices with a CPU and non-volatile RAM with a private key, that authenticate themselves to the host via a challenge-response protocol, using the private key to sign the challenge. The private key does not leave the device and should be tamper-proof to some extent. This method is used in credit cards with PIN.
| Attack | Description | Countermeasures |
|---|---|---|
| Cloning | The attacker clones the token by copying the secret key | Use a secure element to store the secret key |
| Replay | The attacker replays the token by intercepting the communication | Use a challenge-response system |
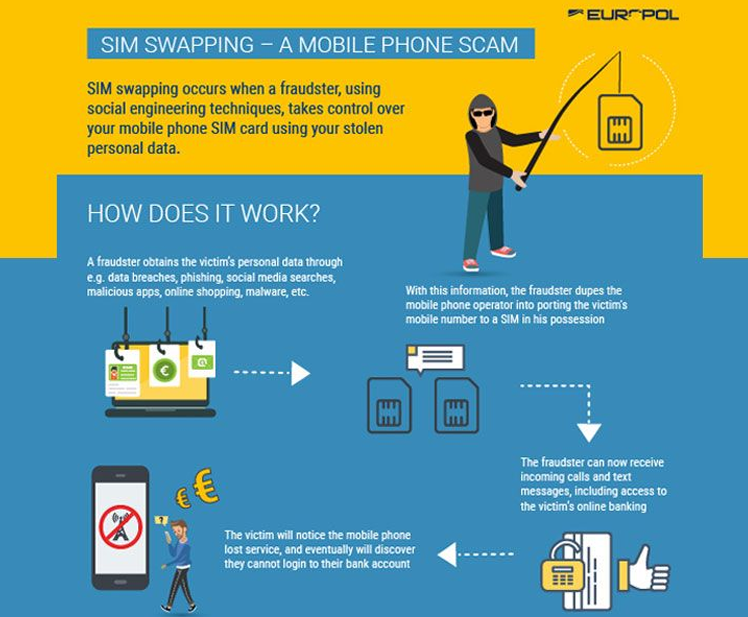
Sim swapping
The sim swapping is a security issue where an attacker fraudulently transfers a victim’s phone number to a different SIM card. This allows the attacker to gain access to the victim’s phone calls, text messages (in particular, an attacker can read clearly all the OTP coming from bank accounts), and other sensitive information.
Sim swapping attacks are often carried out by social engineering techniques, where the attacker convinces the victim’s mobile service provider to transfer the phone number to a SIM card under their control. This can lead to identity theft, financial fraud, and unauthorized access to online accounts.
It is important for individuals to be aware of this threat and take steps to protect their phone numbers, such as using strong authentication methods and being cautious of suspicious requests for personal information.
Something to be - Biometric Authentication
The “to be” factor is based on something that the entity is, like a fingerprint, a face, or a voice. The advantages of this factor are the high level of security and the fact that it requires no extra hardware to carry around. The disadvantages are that it can be hard to deploy, the matching is probabilistic, the measurement can be invasive, it can be cloned, the bio-characteristics change, it is privacy-sensitive, and that it can be difficult for users with disabilities. Countermeasures for biometric authentication are really difficult to implement, because they rely on the physical characteristics of the user. The only possibility is to re-measure often the characteristics, to secure the process, and to provide an alternate (weaker) authentication method for users with disabilities. However, this process might have huge impact on usability.
Examples of biometric authentication technologies are:
- fingerprints: the features of the fingerprint are extracted during the enrollment process, and compared during the authentication process. The sample is taken by a fingerprint reader, and the features are derived from the sample. The feature vectors are stored in a secure database, and when the user logs on, a new reading of the fingerprint is taken and compared against the reference features. The main issue with this technology is the false positives and false negatives.
- face geometry: the features of the face are extracted during the enrollment process, and the features are compared during the authentication process. The main issue with this technology are again the false positives and negatives.
- retina/iris scan
- voice analysis and typing dynamics
- DNA
Nowadays, there are many consumer-level biometric authentication systems available on the market, like fingerprint readers and face recognition systems, implemented in mobile devices and laptops. These systems are used to provide a second factor of authentication, in addition to the traditional password or PIN, improving the security of the system and the overall user experience. However, these systems are not perfect and can be cracked, as shown by the Chaos Computer Club in 2013, when they broke the Apple TouchID system.
| Attack | Description | Countermeasures |
|---|---|---|
| Spoofing | The attacker uses a fake biometric sample | Use a liveness detection system |
| Replay | The attacker uses a recorded biometric sample | Use a challenge-response system |
Single sign on (SSO)
Definition
Single sign-on is a method of authentication that allows a user to access multiple applications with one set of credentials. The user authenticates once on a trusted host, and the other hosts ask the trusted one if the user is authenticated.
This method is used to simplify the authentication process and reduce the number of passwords that a user has to remember. There are several implementations of single sign-on:
- Shibboleth is an example of a single sign-on system used in universities and research institutions. In this system, the user authenticates once on the identity provider (like Aunicalogin), and the service provider (like WeBeep) can access the user’s information.
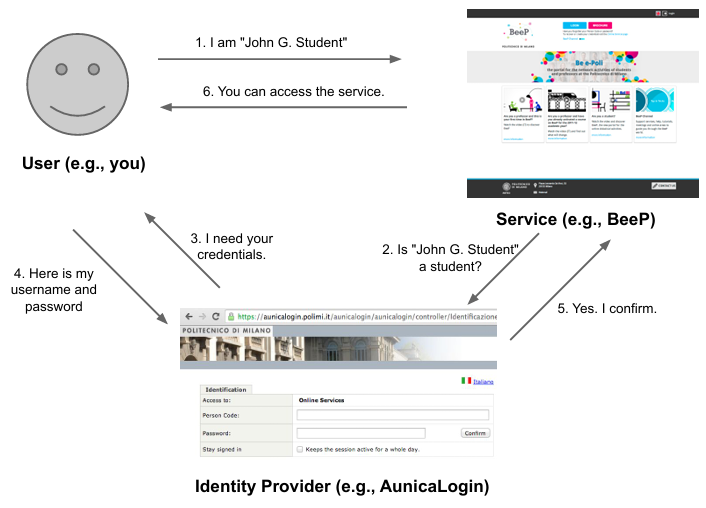
- OAuth2 is an example of a single sign-on system used by social media platforms like Facebook. In this system, the user authenticates once on the identity provider (like Facebook), and the service provider (like a third-party app) can access the user’s information.
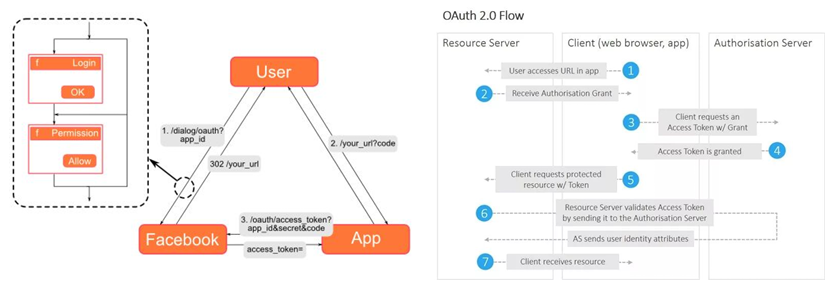
Social media introduces these systems to provide a seamless user experience and improve security. However, they can collect a lot of personal information about the user, information that come from other services and sites, that can be merged together to create a detailed profile of the user. This can be a privacy concern for the user, as the information can be used for targeted advertising or other purposes. System like Shibboleth, however, are more secure and privacy-friendly, as they are used in academic and research environments, where the privacy of the user’s information is a top priority and they do not collect personal information about the user.
SSO systems have some challenges: it’s necessary to find a trusted server that can handle the authentication process securely and the password reset scheme must be extremely bulletproof; if the trusted server is compromised, all the sites are compromised. It’s also extremely difficult to get right for the developers, as the flow is complex to implement and the libraries that exist can be bugged and not well maintained.